Last year I made a handy little tool called Periscope. It lets you sandbox a web page and see all of what happens, without any risk to your browser. Since I was giving it a little love with some updates and UI improvements recently I decided it was high time I made a post about it 😊
Periscope is a CentOS/Red Hat targeted web app, written in NodeJS. Behind the scenes it runs an instance of Chromium (or Chrome) using the automation APIs (specifically the Puppeteer library) to drive that browser to a site of your choosing; then it records the resulting requests and responses.
The core of the app is a HTTP API with options to add a new site to be sandboxed, and retrieve the results.
> curl -XPOST http://localhost:3000/targets/add -H "Content-Type: application/json" -d '{"url": "https://httpstat.us/418"}'
{
"visit":{
"visit_id":301,
"target_id":60,
"createtime":"2021-01-08T19:04:02.000Z",
"time_actioned":null,
"completed":false,
"screenshot_path":null,
"status":"submitted",
"settings":{
"viewport":{
"width":1903,
"height":1064,
"hasTouch":false,
"isMobile":false,
"isLandscape":true,
"deviceScaleFactor":1
},
"userAgent":"Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/88.0.4324.182 Safari/537.36 Edg/88.0.705.74"
}
}
}On top of this is a user interface in VueJS and Bootstrap, written to be responsive and mobile-friendly, and intuitive to use.
Features include:
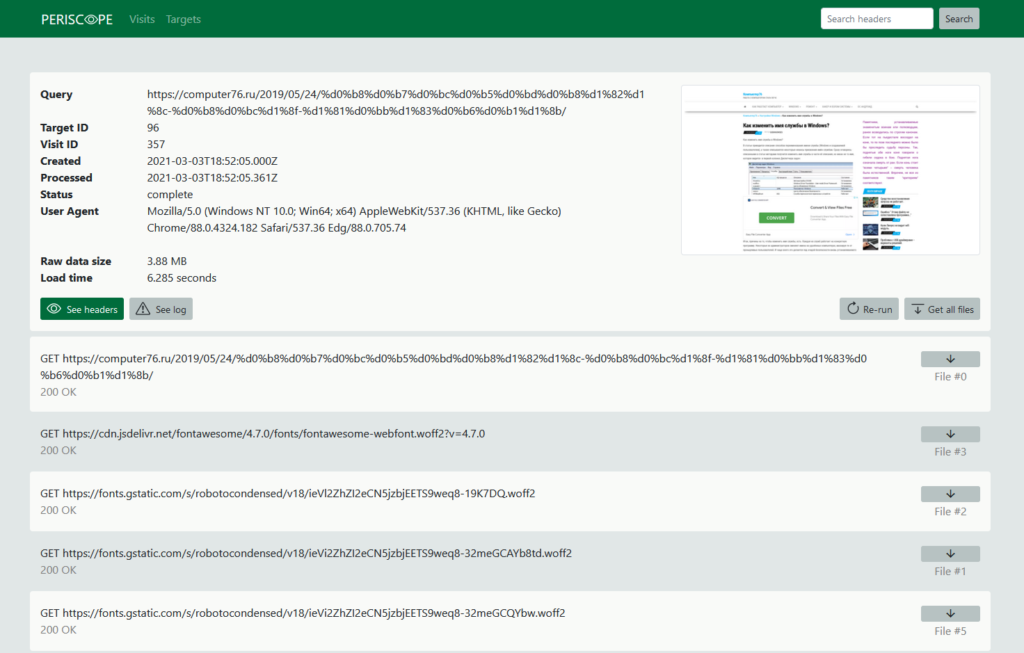
- Capturing a screenshot of the page
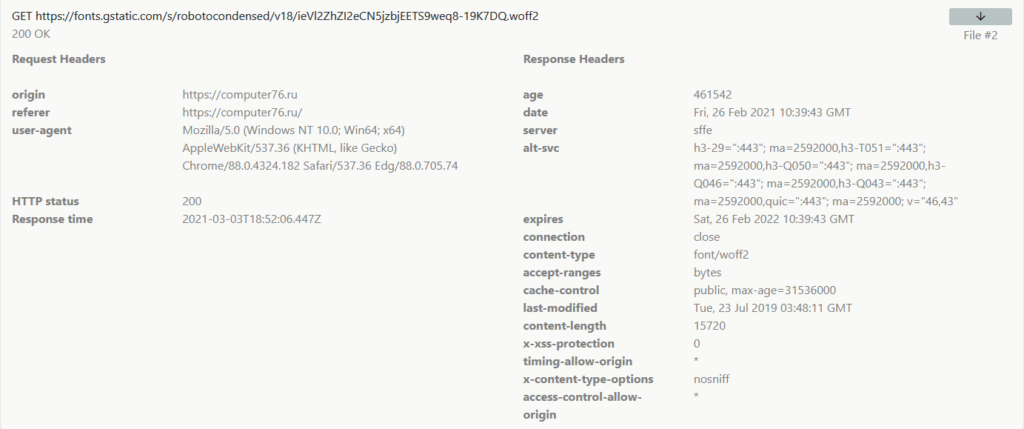
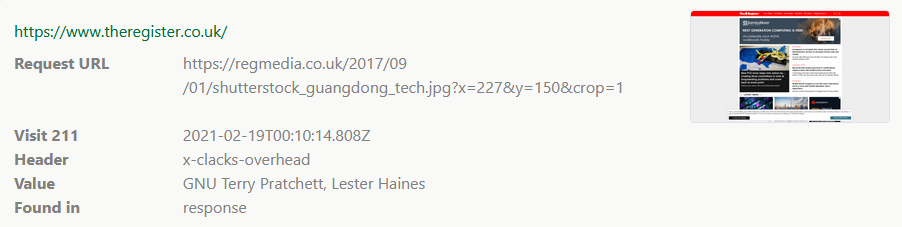
- Recording all headers (names and values) in every request and response
- Recording HTTP POST parameters
- Storing full content of all results, downloadable by the user either individually or as a set (.tar.gz archive)
- Indexed search of the header names and values
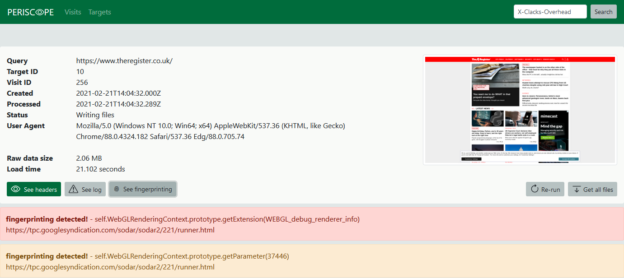
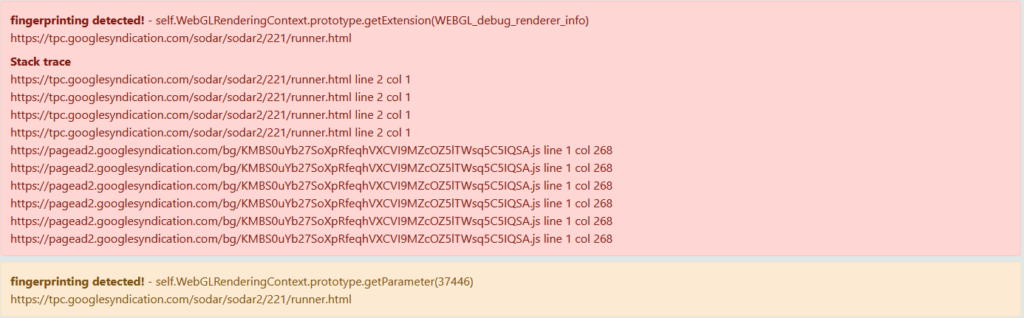
- Using the Don’t FingerPrint Me extension to alert on attempts to fingerprint the browser
All of this lovely stuff is available for free (MIT license) on GitHub. Enjoy!